How To Use Ansible roles for remote management From Satellite Server
- Munshi Hafizul Haque

- Aug 9, 2020
- 3 min read
Updated: Oct 3, 2021
As we can use Ansible roles for remote management in the target system from Satellite Server. And in terms of remote management, we can do OS Hardening, Configuration Management and so on using the Ansible playbook roles. let start with OS Hardening example.
Step:1 To verify the yum repository for the Red Hat Enterprise Linux System Roles.
# subscription-manager repos --enable=rhel-7-server-extras-rpms
or
# yum repolistStep:2 To install the rhel-system-roles package in the Satellite Server.
# satellite-maintain packages install rhel-system-rolesNote: It will take a while, and for more details regarding Red Hat Enterprise Linux System Roles: https://access.redhat.com/articles/3050101
Step:3 To download RHEL7 Hardening Ansible Playbook role, as below.
# cd /usr/share/ansible/roles/
# git clone git@github.com:mh2ict/RHEL7-CIS.git
Cloning into 'RHEL7-CIS'...
remote: Enumerating objects: 43, done.
remote: Counting objects: 100% (43/43), done.
remote: Compressing objects: 100% (40/40), done.
remote: Total 958 (delta 6), reused 19 (delta 0), pack-reused 915
Receiving objects: 100% (958/958), 347.64 KiB | 218.00 KiB/s, done.
Resolving deltas: 100% (537/537), done.
# ls -la
::::::::::::: CUT SOME OUTPUT :::::::::::::
drwxr-xr-x. 9 root root 159 Aug 9 13:38 project-receptor.satellite_receptor_installer
drwxr-xr-x. 10 root root 175 Aug 9 13:38 RedHatInsights.insights-client
drwxr-xr-x. 14 root root 4096 Aug 12 06:36 RHEL7-CIS
drwxr-xr-x. 9 root root 137 Aug 12 05:58 rhel-system-roles.kdump
drwxr-xr-x. 9 root root 4096 Aug 12 05:58 rhel-system-roles.network
drwxr-xr-x. 6 root root 95 Aug 12 05:58 rhel-system-roles.postfix
drwxr-xr-x. 8 root root 119 Aug 12 05:58 rhel-system-roles.selinux
drwxr-xr-x. 10 root root 213 Aug 12 05:58 rhel-system-roles.storage
drwxr-xr-x. 11 root root 168 Aug 12 05:58 rhel-system-roles.timesync
drwxr-xr-x. 8 root root 201 Aug 9 13:38 theforeman.foreman_scap_clientStep:1 To distribute SSH keys manually, and enter the following command on Satellite Server (or if any Capsule), as below.
# ssh-copy-id -i ~foreman-proxy/.ssh/id_rsa_foreman_proxy.pub root@192.168.122.12
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/usr/share/foreman-proxy/.ssh/id_rsa_foreman_proxy.pub"
The authenticity of host '192.168.122.12 (192.168.122.12)' can't be established.
ECDSA key fingerprint is SHA256:kqo2xEmDGgPqXnryZ0Vx1ORyDi3/CGZHgy6UWUm/AaQ.
ECDSA key fingerprint is MD5:9d:ea:1d:bc:38:e7:ee:eb:8d:41:9b:25:cf:6d:62:7f.
Are you sure you want to continue connecting (yes/no)? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
Authorized uses only. All activity may be monitored and reported.
root@192.168.122.12's password: *******
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.122.12'"
and check to make sure that only the key(s) you wanted were added.
# ssh -i ~foreman-proxy/.ssh/id_rsa_foreman_proxy root@192.168.122.12 dateNote: I do not have any separate Capsule server, that's why I ran it from the Satellite Server. And we need to repeat for each target host that we want to manage. for me only one host.
Ansible Role Configuration:
Step:1 In the Satellite web UI, navigate and click Configure > Roles, as below.

Step:2 And click the Satellite Server (or if any Capsule) that contains the roles, as below.

Step:3 And click the Satellite Server (or if any Capsule) that contains the roles, as below.

And finally, RHEL7-CIS roles will be listed in the imported Ansible Roles, as below.

Now, We can assign the RHEL7-CIS Ansible Roles to the target hosts or host groups.
Assign Ansible Roles & Run in the Target System:
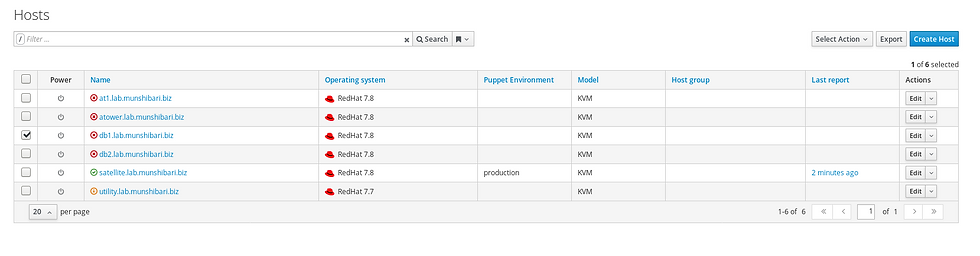
Step:1 In the Satellite web UI, navigate and click Hosts > All Hosts, as below.

Step:2 On the db1 host that we want to assign an Ansible role. Click Edit, as below.
Step:3 Select the Ansible Roles tab. Click "+" in the Available Ansible Roles, as below.

Verify the Assigned Ansible Roles and Click Submit, as below.

Step:2 To run Ansible Roles on a Target Host,
In the Satellite web UI, navigate to Configure > All Hosts.
Select the checkbox of the host that contains the Ansible role you want to run.
From the Select Action list, select Run all Ansible roles, as below.

Or, from the db1 host details windows, Select Run Ansible roles from the Schedule Remote Job, as below.

Click db1 hyperlink and view the status of the Ansible job on the Run Ansible roles page.

The status of the Ansible job.

The Ansible job has successfully completed.

Troubleshooting:
Make sure the Satellite Server (or if any Capsule) can successfully resolve the db1 hostname.
Ensure that the SSH key has properly copied
And also ensure the configuration of any network or host-based firewalls to enable access to port 22
Hopefully, this post will help.















Comments